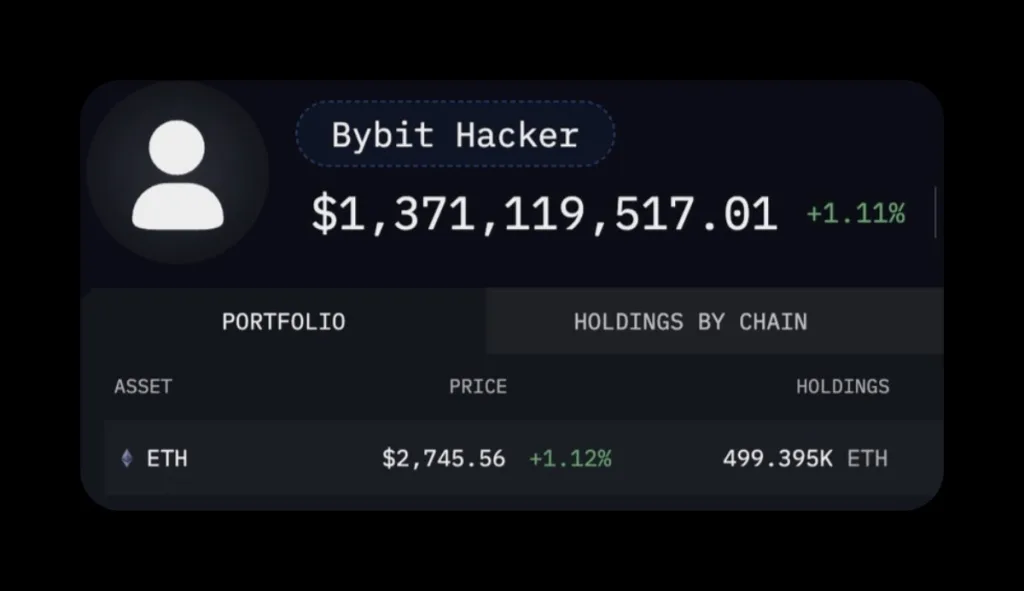
The cryptocurrency exchange Bybit was hacked yesterday, February 21, 2025, resulting in losses exceeding $1.46 billion. This staggering amount represents approximately 16% of all funds stolen in previous crypto hacks combined, making it one of the largest cryptocurrency heists in history. According to blockchain investigator ZachXBT, the attack has been attributed to Lazarus Group, a notorious hacking organization with ties to North Korea.
Breach Timeline and Fund Movements
The breach came to light when ZachXBT reported “suspicious outflows” from Bybit, totaling over $1.46 billion. Shortly after the initial reports, unusual activity was observed on decentralized exchanges, where mETH and stETH were being swapped for ETH. The attacker then escalated their efforts, splitting 10,000 ETH across 39 different addresses and another 10,000 ETH across 9 additional addresses.
According to on-chain data, funds were quickly laundered through various mixing services, including Tornado Cash, which has previously been used by Lazarus Group for obfuscating stolen crypto transactions. Investigators have traced portions of the stolen ETH moving toward exchanges known for lax KYC policies, suggesting attempts to cash out funds via secondary markets.
Sophisticated Social Engineering Bypasses Multi-Signature Security
Unlike previous high-profile crypto hacks that exploited smart contract vulnerabilities, this breach was executed through a highly sophisticated social engineering attack. Instead of targeting Bybit’s code, the hacker exploited human weaknesses within the exchange’s security infrastructure.
Each individual responsible for signing multi-signature transactions was presented with what appeared to be a legitimate interface from Safe, a widely used wallet infrastructure provider. Unbeknownst to them, they were not approving standard transactions but were instead authorizing changes to the logic of their ETH cold wallet’s smart contract.
Breakdown of the Attack Methodology:
- Identifying each multi-signature signatory through social engineering and phishing attempts.
- Infecting the devices of each signatory with malware, likely through spear-phishing emails or compromised software downloads.
- Manipulating the interface to display a different transaction than the one actually being signed.
- Gaining approval from all signatories without raising suspicion, thereby bypassing Bybit’s multi-signature security system.
Security experts suggest that the malware used in this attack could be similar to those previously deployed by Lazarus Group, such as AppleJeus, which targets crypto exchange employees.
Bybit Assures Users of Financial Stability
Despite the massive breach, Bybit has assured its users that the platform remains solvent. In an official statement, the exchange confirmed:
“Bybit remains financially stable, even if the losses from this hack are not recovered. All client assets are backed 1:1, and we are capable of covering the losses.”
The exchange also clarified that only its ETH cold wallet was compromised, while its hot wallet and other cold wallets remain secure. Reports indicate that Bybit has already begun collaborating with law enforcement agencies, including Interpol and blockchain analytics firms, to track the movement of stolen funds.
Safe Team Collaborates with Bybit, No Frontend Compromise Detected
The security team at Safe, the wallet infrastructure provider, has been working closely with Bybit to investigate the incident. In a statement, Safe confirmed:
“We have found no evidence that the official Safe frontend code was compromised. However, as a precautionary measure, certain functionalities have been temporarily suspended.”
This suggests that the attack was conducted through an external phishing operation rather than a direct compromise of Safe’s platform.
Implications for Cryptocurrency Security
This hack exposes critical vulnerabilities in cryptocurrency security management. Key takeaways include:
- Multi-signature systems are not foolproof if human signatories can be compromised.
- Cold wallets do not guarantee absolute security if transaction approvals are manipulated.
- Even with secure code, humans remain the weakest link in the security chain.
- Supply chain attacks are becoming increasingly sophisticated, with hackers targeting individuals rather than systems.
Security Recommendations
In light of this breach, security experts recommend the following measures to enhance protection:
- Use hardware wallets with screen verification to ensure transaction accuracy.
- Implement multi-layered authentication beyond multi-signature approvals, such as biometric or behavioral verification.
- Enforce strict operational security (OpSec) policies for employees handling crypto transactions.
- Conduct continuous security training for employees to recognize phishing attempts.
- Monitor and audit transactions in real time using AI-powered anomaly detection systems.
The Road Ahead for Bybit
If Bybit successfully navigates this crisis, it could strengthen trust in the broader cryptocurrency ecosystem by demonstrating resilience. However, if the exchange fails to recover, it risks becoming the largest exchange failure since the collapse of FTX. This incident serves as a stark reminder of the evolving threats in the crypto space and the need for continuous innovation in security practices.
As the investigation continues, the crypto community will be closely watching how Bybit addresses the fallout from this unprecedented breach. Law enforcement agencies worldwide have already been alerted, and international cooperation may play a crucial role in tracking down the perpetrators and recovering lost funds.
Updates & Investigation Progress
Authorities, including the FBI and South Korean cybercrime units, have begun probing Lazarus Group’s involvement. Preliminary reports suggest that portions of the stolen funds have been transferred to known Lazarus-controlled wallets. This aligns with previous high-profile crypto heists, such as the 2022 Ronin Bridge exploit, where Lazarus Group stole over $620 million.
The crypto industry now faces renewed scrutiny over the vulnerabilities in multi-signature security models. Exchanges are being urged to integrate additional layers of protection, including hardware-backed authentication and AI-driven anomaly detection.
The coming weeks will be crucial in determining how Bybit and the broader crypto community respond to this historic breach. Stay tuned for further updates as the situation develops.













